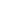How to Prevent DDoS Attacks: Essential Tips
IT Security Updated on : December 31, 2025DDoS is stated as distributed Denial Attack which is a malicious attempt that disrupts normal server, service or network traffic. As per the data available, there was around 30% increase in DDoS attacks in 2024. This states that the number of attacks is rising daily.
Therefore, to help you prevent DDoS attack we have covered essential tips you can follow in 2026. Let’s first understand how DDoS attack works.
Table of Content
How DDoS Attack Works?
As you are aware that DDoS harms your websites, servers, and online services for uses, that make your websites inaccessible to the end user by adding more traffic than they can manage and handle.
Mainly there are three types of attacks:
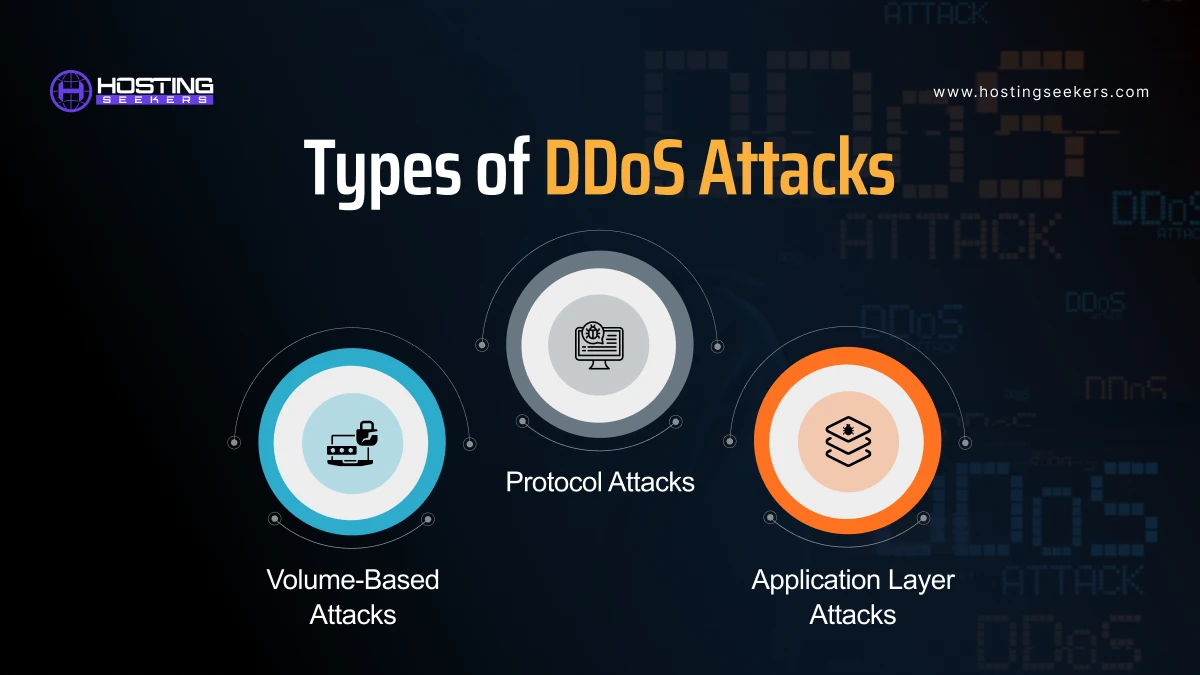
1. Volume-Based Attacks
These are the most common types of attacks. They aim to saturate the bandwidth of the targeted site or networks. Most methods include ICMP floods, UDP floods, and other spoofed-packet floods.
2. Protocol Attacks
These attacks mostly consume server resources or intermediate communication equipment like firewalls and load balancers. Some of the examples are fragmented packet attacks, synchronize message floods, and oversized packed utilized in ping of death attacks.
3. Application Layer Attacks
These are the most stealthy attacks that target particular services or applications. Some examples of this type of attack includes Slowloris attacks, HTTP floods that can impact at the lower request volumes than standard HTTP by opening the server connections.
How to Prevent DDoS Attacks?
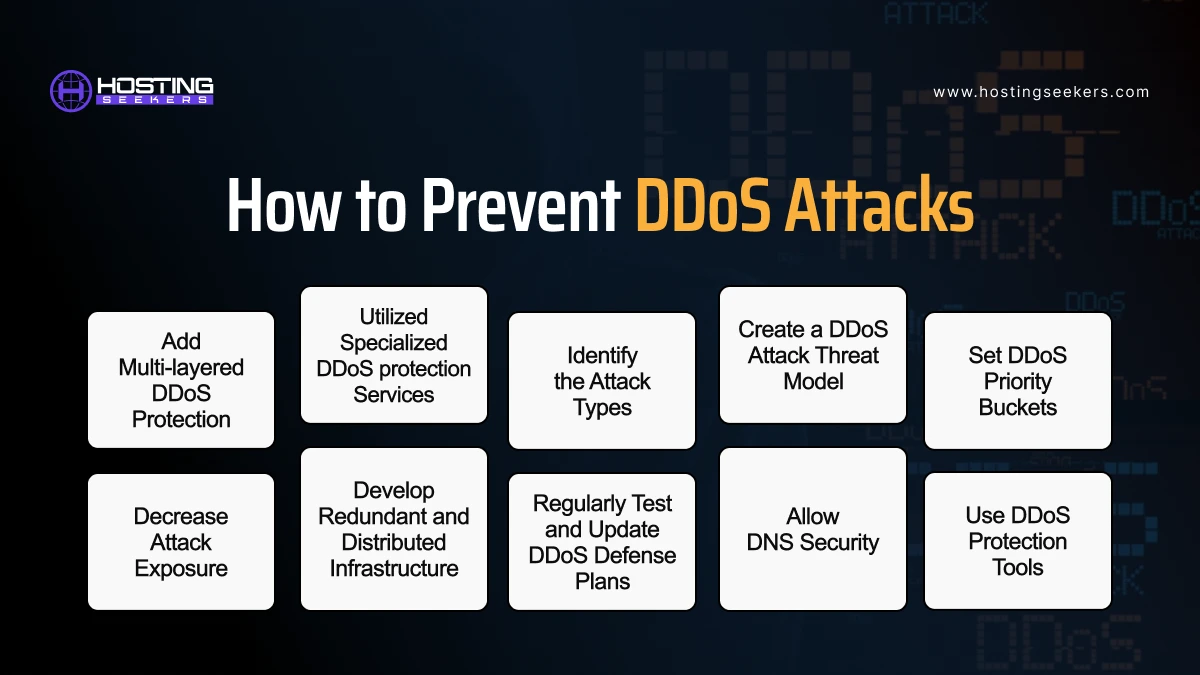
1. Add Multi-layered DDoS Protection
DDoS attacks are not similar to how they used to be 10 years ago. Today, everything has changed and also the way DDoS attacks. Each type of DDoS attacks a different layer like transport layers, network layer, application layer, session layer, combination layers and much more.
In addition, attackers are finding new methods to make websites unavailable to relevant traffic and using methods to exploit vulnerabilities.
Also, preventing DDoS attacks needs more than just rising bandwidth or utilizing standard firewalls. It demands a significant defense against application layer DDoS attacks.
2. Utilized Specialized DDoS Protection Services
Use specialized DDoS protection services like hire experts for your website. These services manage your traffic continuously and utilize robust methods to protect your traffic.
For instances, services like Cloudflare’s DDoS protection or AWS shield can detect and mitigate attacks in real time. These providers have robust global infrastructure that can manage even the biggest attacks.
3. Identify the Attack Types
You should be able to identify the attack type before the attacker. As mentioned, there are three frequent types of attacks that you may identify. Layer 7, Application layer or HTP flooding.
Therefore, by managing and understanding each type of attack, it helps to pay attention to more targeted and impactful defense mechanisms like filtering particular traffic or blocking malicious IP addresses. In addition, early access of the attack type can help you to predict and prevent future attacks and improve overall security posture.
4. Create a DDoS Attack Threat Model
Developing a DDoS threat attack model is vital for analyzing and identifying potential risk. Start by creating a comprehensive database of all web assets you wish to protect against DDoS attacks. This inventory sheet must include network details, protocols in use, domains, number of applications, last updated version and other vital info.
Moreover, identify the different attack that an attacked may use to launch a DDoS attack. Common attack vectors incorporate UDP flooding, SYN flooding or HTTP flooding.
5. Set DDoS Priority Buckets
Start with particular the priorities and criticality of your web resources for enhancing DDoS Security. For instance, business and data-centric web assets should be under the critical bucket with 24/7 DDoS protection.
Put all the assets that can compromise business transactions or your reputation. Hackers have high motivation to target these resources first. Moreover, this bucket must include web assets that can impact daily business operations.
6. Decrease Attack Exposure
To decrease the risk of DDoS attacks, it is vital to decrease the surface area exposed to attackers. You can segment the network by separating and distributing assets within your network to make them harder to target. For instance, you can place web servers in a public subnet while keeping database servers in a private subnet.
You can also restrict the traffic to your website or apps from countries where your users are situated. This restricts traffic to potential attackers from regions where legitimate users are not expected.
7. Develop Redundant and Distributed Infrastructure
Geographic distribution and redundancy are the vital factors to deal with DDoS attacks. Distribute traffic across multiple servers, reducing the impact on any single location.
Host resources in multiple data centers worldwide to absorb attack traffic impactfully.
8. Regularly Test and Update DDoS Defense Plans
A outdated plan can be vulnerable to DDoS attacks. Continuously updating and testing these plans can make sure that your organization for evolving threats.
Therefore, conduct regular drills to analyze the response and also conduct the gap analysis in defenses. Moreover, continuously track and update tools to counter new attack vectors.
9. Allow DNS Security
Mostly DNS servers are more vulnerable to DDoS attacks, therefore, use DNS defense strategies like deploying multiple servers through different regions. Monitor traffic continuously for unusual activity or patterns indicative of attacks. Moreover, use DNSSEC which is Domain Name System security extensions to validate DNS responses to prevent tampering and spoofing.
10. Use DDoS Protection Tools
Effective DDoS mitigation hinges on the ability to identify and neutralize malicious traffic surges before they inflict significant harm, regardless of the attack layer.
Modern DDoS protection solutions stand out for their swift detection and resolution of fake traffic, leveraging a variety of proactive strategies to safeguard your digital infrastructure.
These tools employ advanced techniques such as real-time traffic monitoring, anomaly detection, behavioral analytics, and traffic filtering to protect against disruptions across all layers of potential attacks.
Conclusion
Implementing the 10 best practices outlined above is crucial to building a resilient defense against DDoS attacks. From regular traffic monitoring and deploying firewalls to leveraging AI-driven anomaly detection and maintaining a strong incident response plan, these measures can significantly minimize the risk of disruptions to your online assets.
However, comprehensive DDoS protection often requires specialized expertise and advanced tools. To further enhance your defenses, consider exploring professional DDoS protection service providers who can offer tailored solutions to safeguard your critical resources against evolving threats.
Frequently Asked Questions
Q 1. How can a DDoS attack be prevented?
Ans. DDoS attacks can be prevented by implementing robust network security measures such as installing CSF firewall, intrusion detection systems, traffic filtering, rate limiting, and real-time monitoring. Employing cloud-based DDoS protection services is also an effective way to mitigate large-scale attacks.
Q 2. What is the best solution for DDoS attack?
Ans. The best solution combines proactive monitoring, behavioral analytics, and automated response systems with cloud-based DDoS protection services. These solutions can identify and neutralize threats swiftly while ensuring uninterrupted service.
Q 3. How are DDoS attacks defended?
Ans. DDoS attacks are defended through traffic filtering, IP blacklisting, deploying web application firewalls (WAFs), and utilizing specialized DDoS mitigation services. Early detection through anomaly monitoring is also critical in preventing damage.
Q 4. What are 3 reasons for DDoS attacks?
Ans. Financial gain: Extortion through ransom demands.
Disruption: Sabotaging a competitor’s operations or damaging a brand’s reputation.
Ideological motives: Protest or activism against an organization.
Q 5. What is a DDoS protection solution?
Ans. A DDoS protection solution is a service or system designed to detect, mitigate, and prevent distributed denial-of-service attacks. It safeguards servers, networks, and applications by filtering malicious traffic and ensuring legitimate requests are served.
Q 6. What is DDoS attack and its prevention?
Ans. A DDoS (Denial-of-Service) attack disrupts a network or server by overwhelming it with excessive traffic from a single source. Prevention includes implementing rate limiting, firewalls, and load balancers, and ensuring redundancy in network infrastructure.
Q 7. Is there a tool to prevent DDoS?
Ans. Yes, many tools and services are available, including cloud-based solutions like Cloudflare, Akamai, and AWS Shield, as well as on-premises appliances such as Arbor Networks and Radware, which help prevent and mitigate DDoS attacks effectively.